Core network architecture is a critical component of cloud infrastructure. It is crucial to establish connectivity among resources and improve application performance. Network architecture plays the most important role in achieving these requirements.
There are certain benefits of network connectivity services in the cloud. These services provide different deployment options to fulfill different workload requirements.
In addition, the Azure network services can be accessed in various countries and are secure, reliable, and resilient.
Azure networking services offer superior performance for expanding applications. These services cater to the applications that have the most demanding availability requirements along with unprecedented security. The resources can be managed easily with Azure network services.
Types of Core Networking Services
a. Network Connectivity & Monitoring Services
The on-premise resources and Azure resources can be connected using various Azure services. In addition, Azure offers monitoring of network resources through different services as well.
Connectivity is offered through VNet, ExpressRoute, Virtual network NAT Gateway, Virtual WAN, VPN Gateway, Azure DNS, Azure Bastion, and Peering service. Monitoring is offered through Network Watcher, Azure Monitor, ExpressRoute Monitor and VNet TAP.
b. Application delivery & protection services
The services in Azure network that deliver applications include CDN, Azure Front Door, Application Gateway, Traffic Manager, Load Balancer, and Internet Analyzer.
Azure services that protect applications include Lload Balancer, DDoS protection, Private link, Firewall, Web Application Firewall, Network Security Groups, and Virtual Network Endpoints.
Benefits of Azure Networking Services
With the help of Azure networking, we can avoid the unnecessary pressure of building and managing network connectivity down to the fiber. It makes traffic management for applications much easier, defines and monitors global routing, offers turnkey firewall capabilities, to name a few among its numerous benefits.
Azure Networking Services
Some of the major networking services that Microsoft Azure offers are discussed below.
Azure Virtual Network
VNet is the basic building block for a Private network in Azure. It can connect Azure resources, establish communication among several VNets, communicate to the internet, and connect resources residing on-premises with those of Azure.
We can have resources within VNet communicate among themselves privately using private IP addresses. We must consider the main concepts of VNet when considering this service, such as address space, subnets, regions, and subscription.
The main design principles that we should consider while using this service are:
- We should ensure that the address spaces of the service do not overlap with that of our organization.
- Our subnet should not cover the whole address space of VNet so that some address space is reserved for the future.
- We should plan ahead to manage overhead by having a few large subnets rather than many small VNets.
- We should assign Network Security Groups to subnets beneath VNets to ensure security.
Azure Load Balancer
This service evenly distributes the load across backend resources like servers. It operates at the fourth layer of the Open System Interconnection model. Here, we need to understand the public as well as the private or internal load balancer.
We can then understand how inbound flows that arrive at the load balancer’s front end are distributed to the backend pool instances.
We can use outbound connections for VMs inside our Virtual network using a public load balancer. Internet traffic can be load-balanced to our VMs through public load balancers.
When we need private IPs for the frontend, we should use an internal load balancer.
Azure load balancer offers fully managed load balancing solutions for different scenarios.
For example, we can balance multi-tier applications using public and private load balancers, as shown in figure 1 below.
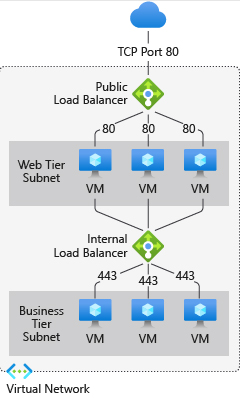
Figure 1: Azure Load Balancer.
Source: https://docs.microsoft.com/en-us/azure/load-balancer/load-balancer-overview
Azure Application Gateway
Azure Application Gateway shall enable us to manage traffic to web applications. It can be better understood as a web traffic load balancer that can help us manage our web applications.
Compared to traditional load balancers that use source and destination IP to route traffic, the Azure application gateway uses additional attributes of the HTTP request to make routing decisions. We can say that it offers OSI layer 7 load balancing.
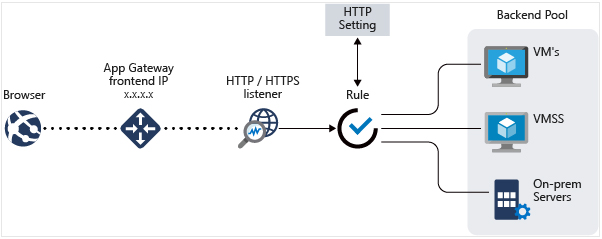
Figure 2: URL path-based routing with Application Gateway.
Azure Virtual Private Network Gateway
Azure VPN Gateway can create encrypted cross-premises connections to virtual networks from on-premises locations or make encrypted connections among VNets.
VPN Gateway offers site-to-site connections, VNet-to-VNet connections, and point-to-site connections, out of which the first one is shown in figure 3 below.
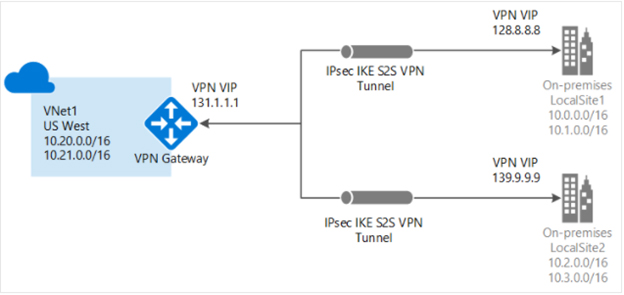
Figure 3: Site-to-site VPN connections to a single virtual network.
Source: https://docs.microsoft.com/en-us/azure/application-gateway/overview
Azure Domain Name System
Azure offers a hosting service for DNS domains that provide name resolution through Azure infrastructure. As a result, we can use the same credentials for managing DNS records that we use for all other Azure services.
Azure Global network of DNS name servers hosts Azure DNS. Therefore, we can get high availability for our domain since queries are answered from the closest DNS server.
We get security features through Azure DNS like Azure role-based access control, activity logs, and resource locking. We can manage DNS records for Azure services as well as for external resources using Azure DNS. It is integrated with the Azure portal, so the same credentials can be used for other Azure services.
Azure Content Delivery Network
Azure CDN caches our content at physical nodes placed worldwide so that the developers can deliver solutions rapidly at high bandwidth. Figure 4 below shows six steps of how Azure CDN works.
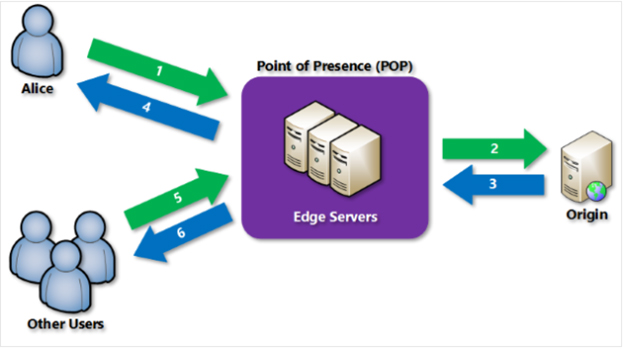
Figure 4: Azure CDN.
Source:https://docs.microsoft.com/en-us/azure/traffic-manager/traffic-manager-routing-methods
Azure CDN service can deliver website assets easily. It provides good performance and user experience even in cases where several round trips are required to load content.
We can handle high instantaneous loads through its scaling feature. It can even distribute user requests and serve from edge servers to reduce traffic to the origin server.
Azure Front Door
We can manage and monitor our global routing for web traffic using Azure’s Front Door Service. It will enable us to put forward modern high-performance applications and expand the audience reach with Azure.
This feature improves global connectivity using anycast protocol with split TCP. The Azure Front Door can route client requests to the fastest and available application considering the routing method that we use.
We can use a range of traffic routing methods offered by Azure Front Door and backend health monitoring options as per our application needs and automatic failover scenarios.
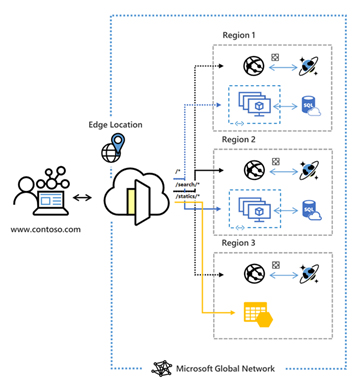
Figure 5: Azure Front Door entry point used by Microsoft global edge network
Source: https://docs.microsoft.com/en-us/azure/private-link/private-link-overview
Azure Traffic Manager
This is a DNS-based load balancer that we can use to optimize traffic to services across global regions of Azure.
We can use several routing methods available in Azure Traffic Manager like priority, weighted, performance, geographic, multi-value, and subnet. These methods can help us determine the network traffic route towards different service endpoints.
This service applies one of the six methods to each DNS query received and that method determines the endpoint that is returned in DNS response.
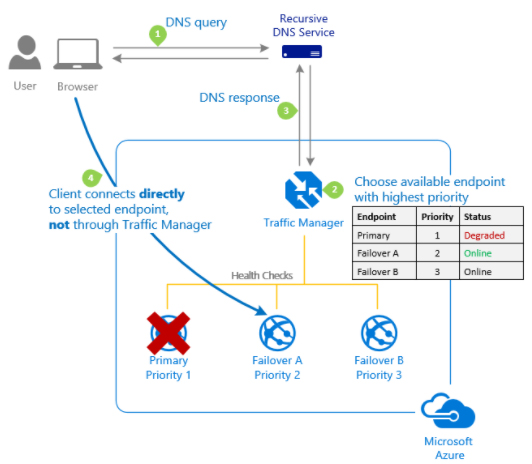
Figure 6: Azure Traffic Manager performing endpoint priority-based routing.
Azure ExpressRoute
Azure ExpressRoute helps us extend on-premises networks into MS Cloud. We can use a private connection to extend the networks with the help of a connectivity provider, as shown in the figure below.
We can build a connection with Microsoft 365 or Microsoft Azure using this service. ExpressRoute does not connect over the public internet, thus offering reliability, consistent latencies, high security, and speed.
We can opt for the ExpressRoute connectivity model according to our needs. The models available include ExpressRoute Direct, Any-to-any IPVPN connection, Point-to-point Ethernet Connection, and CloudExchange Co-Location.
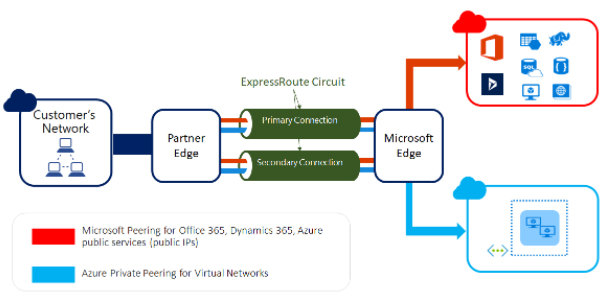
Figure 7: ExpressRoute extending network into MS cloud
Azure Private Link
This is a protection service of Azure that allows access over private endpoints in our virtual network. We can access PaaS services like Azure storage and SQL Database and Azure-hosted services using Azure Private Link.
This service and others like private Endpoint and Private Link services are all generally available. We get several benefits with this service like:
- We can connect our virtual network in Azure even without a public IP address.
- Private Endpoints enable Azure services from on-premises and peered networks.
- It offers protection against data leakage.
- It provides global reach by connecting privately to services running in different regions.
- We can place our service behind standard Azure Load Balancer and enable the service for Private Link.
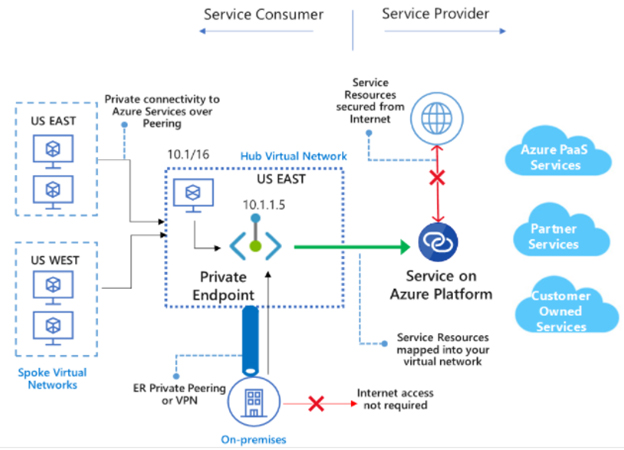
Figure 8: Accessing PaaS Services through Azure Private Link.
Azure Network Watcher
Azure Network Watcher provides monitoring and diagnostic tools for metrics and logs for resources in Azure VNet. It shall monitor and repair the IaaS products that have VMs, NNets, load balancers, etc.
Monitoring
- The service monitors communication between VM and endpoint.
- It views resources in VNet and understands their relationship through its topology capability.
Diagnostics
- It can diagnose the network routing issues and traffic filtering issues to and from the VMs.
- It can capture packets to and from VM and troubleshoot outbound connections from VM.
- Using its VPN diagnostic capability, it can diagnose availability and issues with gateways and connections.
- It can calculate latencies between ISPs and Azure regions.
- Lastly, its diagnostic logs capability can enable/disable network diagnostic logs for an existing network resource that generates logs.